Evolving Red Team C2: From Stealth Agents to Trusted Applications.
Don't trust me, I am Evilraptor.
Read MoreStay informed on the latest threats, vulnerabilities, and defensive strategies with insights from the Hackyde team.
 Offensive Security
Offensive Security
Don't trust me, I am Evilraptor.
Read More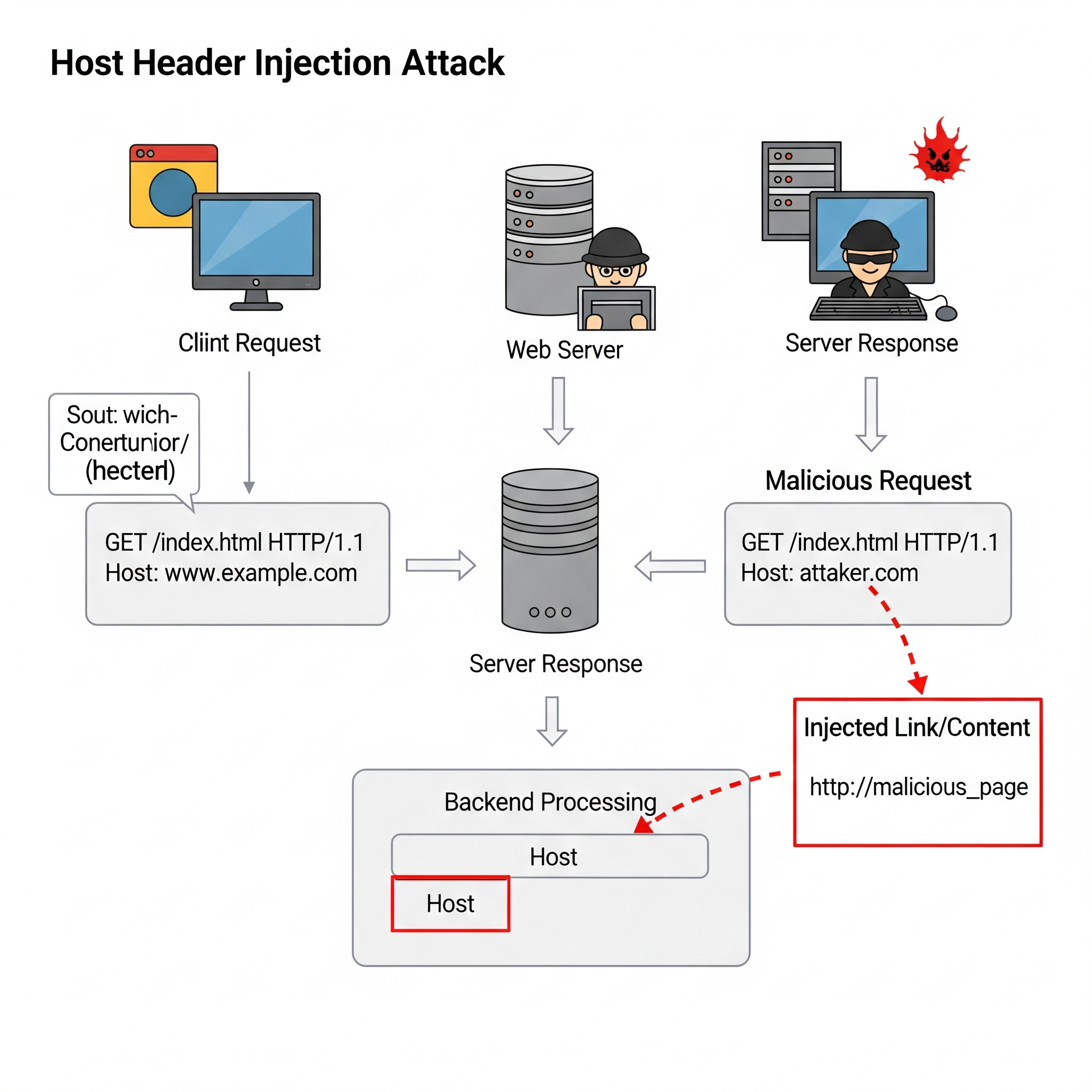 LiquidFiles Zero Day Vulnerability
LiquidFiles Zero Day Vulnerability
A Red Team Perspective on Redirection Attacks.
Read More AI/LLM Breach
AI/LLM Breach
How Tenable was affected by the recent Salesloft Drift AI application breach.
Read More Attack Simulation
Attack Simulation
An insider threat—whether malicious or accidental—can be one of the most damaging and difficult security incidents to handle.
Read More Incident Response
Incident Response
An insider threat—whether malicious or accidental—can be one of the most damaging and difficult security incidents to handle.
Read More Offensive Security
Offensive Security
Understand the critical difference between a standard penetration test and a true red team exercise, and find out which one is right for you.
Read More Cloud Security
Cloud Security
Discover the most common and dangerous misconfigurations in AWS that our team finds, and learn how to secure your cloud environment proactively.
Read More Social Engineering
Social Engineering
We break down the sophisticated tactics used by attackers in modern phishing campaigns, from QR code exploits to AI-powered lures.
Read More